
Never Trust, Always Verify: How AstraOps Brings AI-Driven Zero Trust Security to Your Multi-Cloud Environment
Revolutionizing Cloud Security with Intelligent Zero Trust Architecture
AstraOps Team
Published: Aug 14, 2025
The old security playbook is officially broken. For decades, we relied on building a strong digital fortress, assuming that anyone inside the walls was a trusted user. But in today's world of remote work and complex multi cloud architectures, that perimeter has vanished. Threats can just as easily come from within as they can from the outside.
This is where Zero Trust Architecture (ZTA) comes in. It's a modern cybersecurity framework built on a simple but powerful principle: "never trust, always verify."
In a multi cloud world, where organizations use services from AWS, Azure, GCP, and more, securing diverse environments is incredibly complex. ZTA provides a strong foundation by treating every access request with suspicion and verifying it explicitly.
And this is where AstraOps stands out.
Our platform doesn't just support Zero Trust, it elevates it by embedding AI powered, ZTA aligned capabilities directly into the fabric of multi cloud management.
The Core Principles of Zero Trust
(and How AstraOps Implements Them with AI)
A Zero Trust model requires continuous verification, least privilege access, and real-time monitoring across every layer of your IT ecosystem. Here's how AstraOps puts these principles into action, powered by AI.
Enforce Least Privilege Access with Behavioral AI
In a Zero Trust model, users are granted access solely to the specific resources they are authorized to use. While this was traditionally enforced with Role-Based Access Control (RBAC), AstraOps takes it a step further with Fine-Grained Access Control (FGAC).
Managing permissions at scale will be overwhelming, which is why AstraOps will have the capability to showcase an AI driven behavioral analytics to:
Predictive Access
The AI will analyze historical usage patterns to suggest optimal access levels for users and services. It will learn what "normal" behavior looks like for each role and automatically flag dormant or excessive permissions for review.
Dynamic Privilege Adaptation
As team roles and projects evolve, the AI will adapt access control policies in real time, ensuring privileges remain lean and secure without constant manual intervention.
With centralized user management and activity logging, administrators gain unparalleled visibility and precise control, and AI keeps those privileges lean and secure.
Mandate Continuous Verification with Dynamic Policy Engines
A single login is no longer enough in a Zero Trust model. Every request must be verified in real time.
AstraOps serves as a unified Policy Enforcement Point across your cloud environments. It ensures that infrastructure remains compliant with your governance models—whether that's SOC 2, ISO 27001, HIPAA, or your own internal benchmarks.
Thanks to AI-powered policy engines, AstraOps can:
Interpret and Automate
The AI interprets complex compliance rules and automatically translates them into actionable policies. It auto-enforces these policies during infrastructure provisioning, so your environment is secure and compliant from day one.
Instant Violation Detection
The system continuously monitors for policy violations and detects them instantly—even when they're hidden in nuanced configurations that a human might miss.
AstraOps also integrates with robust Identity and Access Management (IAM) systems, like AWS Cognito, ensuring that only authorized users get access within the scope they're allowed.
3. Assume Breach and Defend Proactively with AI-Powered Guardians
Zero Trust operates on the assumption that breaches will happen. AstraOps enables teams to act before damage occurs, using AI to drive intelligent defense mechanisms.
A key example is AI-driven drift detection. AstraOps continuously monitors live infrastructure against your approved High-Level Design (HLD) blueprint. When unauthorized changes are detected, the AI:
- Provides Intelligent Alerts: It instantly alerts the admin and uses its analysis to suggest whether the drift is a safe, suspicious, or likely malicious change.
- Offers Auto-Reversion: It gives you the option to automatically revert the infrastructure to its secure baseline, stopping a potential attack in its tracks.
This turns AstraOps into an AI-powered guardian for your cloud that is capable of establishing a subtle misconfigurations before they become major risks.
The AI-Driven Difference: Compliance from Code to Cloud
Security and compliance shouldn't be afterthoughts and they should be a core part of the build process.
AstraOps makes this possible with AI-first compliance enforcement. As you visually design infrastructure:
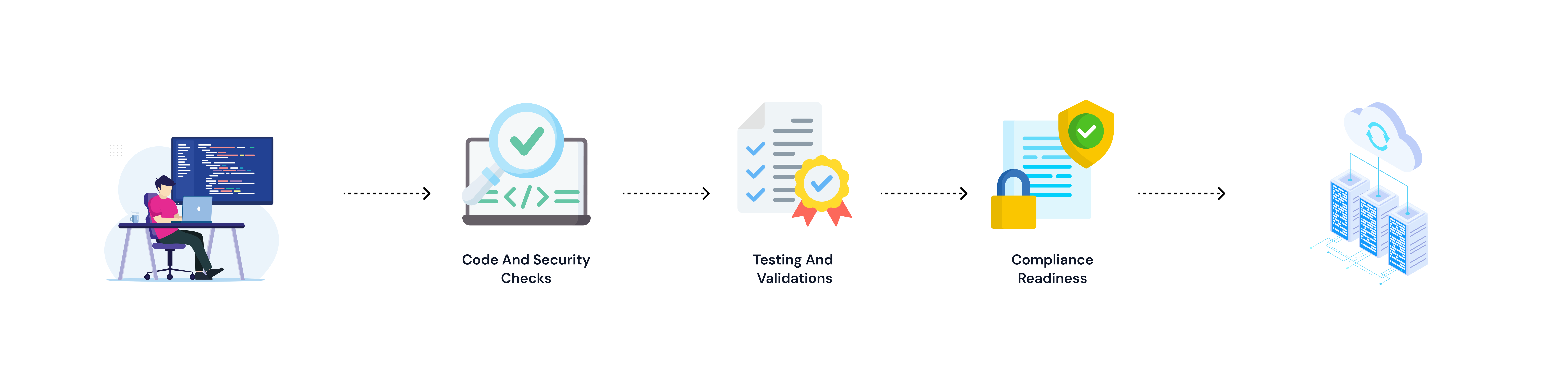
- Pre-Deployment Audits: We notify users of compliance violations before deployment and continuously monitor for compliance drifts even after deployment. The system acts as a smart advisor, guiding you to a secure configuration.
- Continuous Learning: The platform learns from previous builds and security incidents to refine its enforcement engine, making it smarter and more effective over time.
"AstraOps embeds these compliance rules directly into the infrastructure deployment process. Our AI-powered governance ensures that as you build, you stay within the required frameworks enabled by design, not by accident."
— One of our engineers
The Future of Cloud Security is AI-Driven Zero Trust
AstraOps goes beyond checklists and static controls. It delivers a living, intelligent security layer that scales with your infrastructure and responds in real time.
Whether you're designing infrastructure, deploying across clouds, or defending against threats, AI is your force multiplier and AstraOps is your command center.
Ready to elevate your security posture with an AI-first approach?
Contact us for a personalized demo and see how AstraOps can protect your multi-cloud environment with Zero Trust Architecture.
